The global digital economy requires APIs to connect application-based services to customers, consumers, partners, and employees. Hackers have learned that compromising APIs is easy when they are lightly protected. An API security model is the starting point of a secure API journey. This guide strips away the veneer of industry hype and takes a realistic look at what buyers of API security solutions should look for when performing a product evaluation.
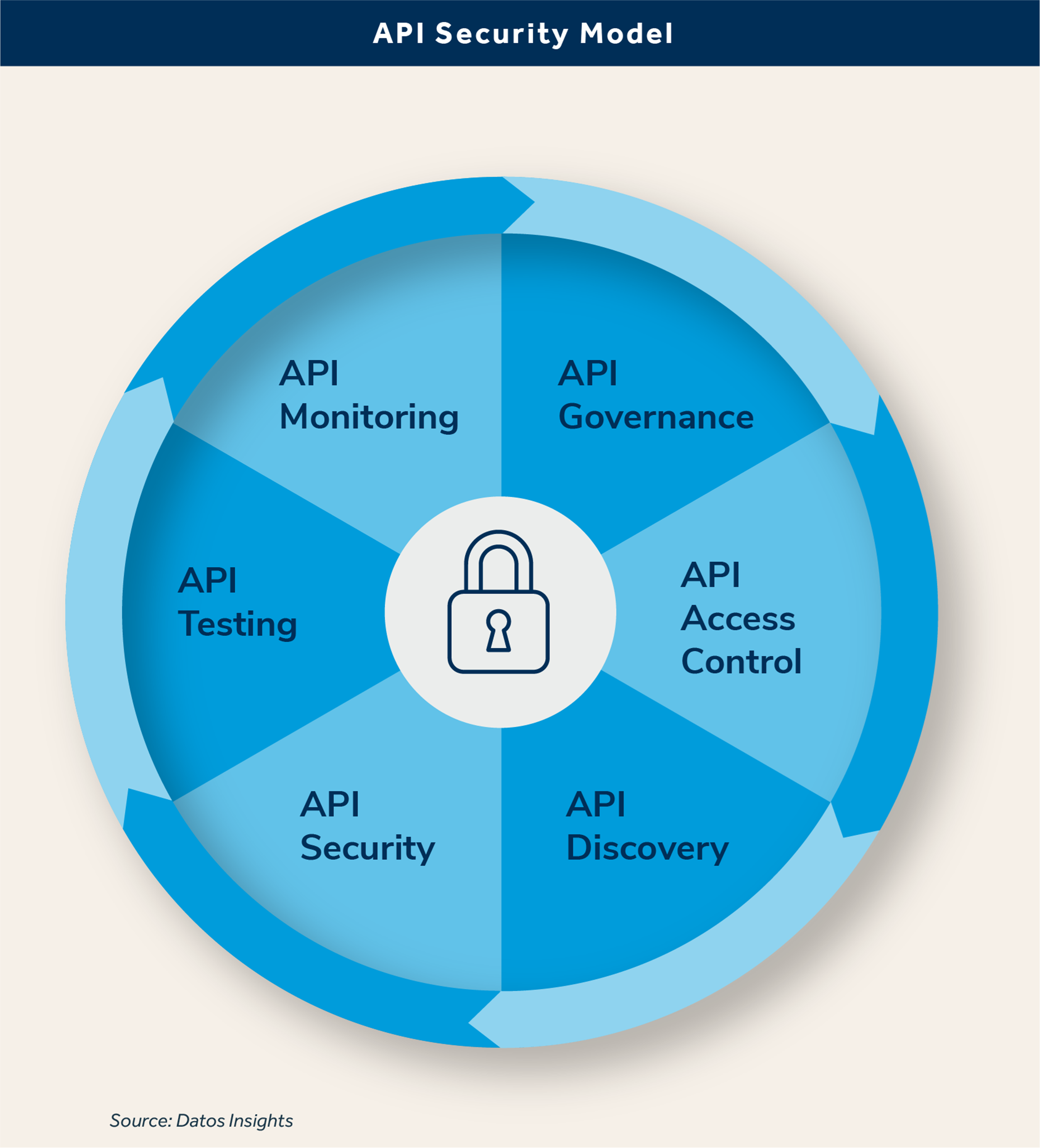
This report describes the various approaches to securing APIs and the important considerations for CISOs and other buyers of API security solutions to help them avoid overspending for solutions that are over- or under-engineered for their needs.
Clients of Datos Insights’ Cybersecurity service can download this report.
This report mentions F5, the Open Web Application Security Project (OWASP), and T-Mobile.
About the Author

Tari Schreider
Tari Schreider, C|CISO, CRISC, ITILf, and MCRP, is a Strategic Advisor at Datos Insights specializing in cybersecurity, information assurance, security program architecture, and maturity improvement. He lives in metropolitan Atlanta and brings more than 40 years of security, privacy, and recovery management to Datos Insights. Tari is an author of top-rated cybersecurity architecture and law books and is a master instructor...
